My #BSidesLV slides: "Mobilizing the PCI Resistance: Lessons Learned From Fighting Prior Wars (SOX-404)"
 Thursday, July 29, 2010 at 11:47AM
Thursday, July 29, 2010 at 11:47AM
I had a great time presenting the work I'm doing with the PCI Scoping SIG to the #BSidesLV community. It was especially gratifying to me that the practitioners in the room agreed so strongly with me on the importance of correct scoping.
Simply put, the success of any PCI DSS compliance initiative is very dependent on accurate definition and scoping of the Cardholder Data Environment and the scope of assessment.


Thank you Mike Dahn (@MikD) and for allowing me to present in your dojo. And I felt incredibly honored when you said that you're already telling your clients that the scoping tools that we're building will likely be the most significant change to the PCI SSC in years.
There is no doubt in my mind that Mike has been one of the top contributors to the PCI DSS body of knowledge, so that kind of endorsement means a lot to me!
Taking Bets On When The "Mike/Josh Hug" Will Occur!
I am also announce that I am taking up the challenge from Josh Corman (@joshcorman) and Mike Dahn (@MikD) to help them "hug it out." Given both of their genuine passion for helping organizations be simultaneously secure and compliant, and their obvious talents, I think I'm up to the task!
I'm starting a pool: who can most accurately predict when "Mike/Josh Hug" will finally occur? The winner will get a framed picture of the hug, signed by both Mike and Josh.
Full Slideshare link below!
Talk abstract:
Properly Mobilizing the PCI Resistance: Lessons Learned From Fighting Prior Wars (SOX-404)"
I have noticed that there is a growing wave of discontent and disenchantment from information security and compliance practitioners around the PCI DSS. Josh Corman has been an effective voice for these concerns, providing an intellectually honest and earnest analysis in his talk “Is PCI The No Child Left Behind Act For Infosec?”
The problem are well-known and significant: too much ambiguity in the PCI DSS, Qualified Security Assessors (QSAs) and consultant using subjective interpretations, existing guidance either too prescriptive or too vague, scope missing critical systems that could risk cardholder data, overly broad scope and excessive testing costs, excessive subjectivity and inconsistency, poor use of scarce resources, no meaningful reduction in risk of data breaches, and so forth.
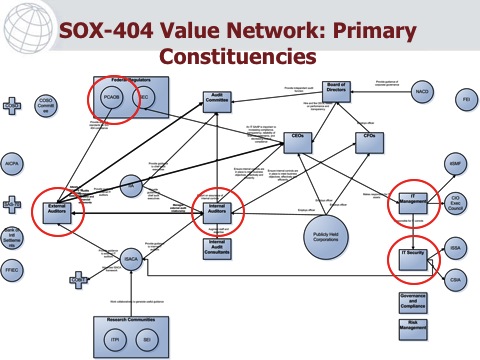
For years, I have been studying the PCI DSS compliance problem, as well. I have noticed many similarities to the PCI compliance challenges and the “SOX-404 Is The Biggest IT Time Waster” wars in 2005. I was part of the leadership team at the Institute of Internal Auditors (IIA) where we did something about the it. We identified inability to accurately scope the IT portions of SOX-404 as the root cause of the billions of dollars of wasted time and effort, while not reducing the risk of financial misstatements.
I propose to present the two-year success story of the IIA GAIT project and how we changed the state of the IT audit practice in support of SOX-404 financial reporting audits. We defined the four GAIT Principles, which could be used to correctly scope the IT portions of SOX-404. We mobilized over 100K internal auditors, the SEC and PCAOBregulatory and enforcement bodies, as well as the external auditors from the 8 big CPA firms (e.g, Big Four and other firms doing SOX advisory work). In short, we made a difference, in a highly political process that involved many constituencies.
I am attempting to do something similar with the PCI Security Standards Council, through my work as part one of the leaders of the PCI Scoping SIG (Special Interest Group). My personal goal is to find a “third way” to better enable correct scoping of the PCI Cardholder Data Environment, and create a risk-based approach of substantiating the effective controls to ensure that cardholder data breaches can be prevented, and quickly detected and corrected when they do occur.
My desired outcome is to find fellow travelers who also see the pile of dead bodies in PCI compliance efforts, and work with those practitioners to catalyze a similar movement to achieve the spirit and intent of PCI DSS.