This is Part 6 of the "Mobilizing PCI Resistance" series. Briefly, we've covered:
The Politics Of SOX-404 And GAIT (And Implications With PCI)
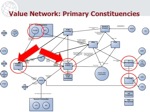
The GAIT project was one of the most politically charged projects I've ever been involved with. The diagram below shows each one of the constituencies, and the relationships between them.
As we go through them, I'll discuss the equivalents to the PCI universe. I posit that while the PCI ecosystem is also very political, it's less so than for SOX-404. This is good news. :-)
My reason for this blog post is to describe how we analyzed the lay of the land, and created a winning strategy that allowed us to change the compliance landscape. By doing this with PCI, we can play to win.
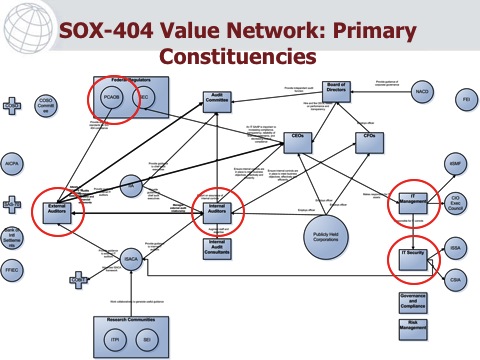
(By the way, this type of diagram is called a "value network," and was taught to me by the famous Eileen Forrester at the Software Engineering Institute at Carnegie Mellon University. Full slides available on SlideShare)
So, let's go through each of primary constituencies, and then I'll discuss how they relate to each other:
The Federal Regulatory Enforcement Bodies:
The Sarbanes-Oxley Act of 2002 was enacted as a response to accounting scandals at WorldCom, Enron, Tyco International, etc.
-
The Securities and Exchange Commission (SEC) created a new set of requirements that public companies (i.e., "SEC registrants") had to comply with.
-
The Public Corporation Accounting Oversight Board (PCAOB) was created by SOX-404, charged with overseeing, regulating, inspecting and disciplining accounting firms in their roles as auditors of public companies.
In other words, they audit the auditors. For instance, on at least an annual basis, they would audit the work papers submitted by the Big Four firms to ensure the quality of their work, and that it's in compliance with the standards of independence. Each year, they would publish a report describing when the external auditors behaved in ways that was "out of line."
The PCI equivalent here is the PCI Security Standards Council and the card brands. The parallels between the PCAOB and the new PCI requirements for QSAs to submit their work papers and Reports on Compliance (ROC) is striking. PCI is now actively auditing the auditors.
The Public Companies:
-
CEOs and CFOs: These are the people specifically named in SOX-404 as personally accountable and responsible for the effectiveness of controls that support the accuracy of the company financial statements (e.g., 10-K statements submitted to the SEC).
When people make jokes about "keep the executives out of orange jumpsuits" or "keep them out of jail," these are the people who would be wearing them.
-
CIOs and IT Management: We identified that one of the primary contributors around the wasted time/effort in support of SOX-404 was in the domain of IT controls. Business management owned the financial controls, and IT management owned the IT controls.
-
Information security: More specifically, many of the IT controls were owned by information security.
The PCI equivalent here are the merchants, service providers, and anyone else who has custodianship of cardholder data. These are the people who are often complaining that the PCI DSS is too subjective, too arbitrary, that the cost of compliance is too high, etc.
And again, this is the likely the community we must mobilize first.
The Internal Auditors
Internal auditors are independent of Business Management and IT Management. Their goal is to ensure that the risks to the organization are understood and that adequate controls exist to prevent, detect and correct for those risks.
(Interestingly, in my experience, in most organizations, internal auditors are only recently showing up at the table for PCI compliance. But, they have a wealth of experience to bring in terms of managing external auditors. And it's my understanding that internal auditors can now submit PCI Reports On Compliance now, even though they're not technically a QSA.)
The External Auditors:
External auditors generate an opinion on the financial statements. They also have their work papers audited by the PCAOB.
The PCI equivalent here are the Qualified Security Assessors (QSAs). Instead of generating an opinion on the accuracy of financial statements, they file a ROC.
Professional Organizations:
The IIA was clearly at the forefront of this issue, and this is the community we mobilized. (ISACA was peripherally involved in the beginning, but dropped out due to unbelievably bad relationships between them and IIA.)
(In the PCI world, I'm not sure if there is a professional organization that we can mobilize. Instead, I believe the best lever is the PCI Community of Participating Organizations.)
Our Resulting SOX-404 Strategy: Start With Internal Auditors, Where Collective Outrage Was Highest
The constituency who probably saw the problems the clearest were the internal auditors, who saw that the amount of investment in IT controls were way out of proportion to the risk. While other constituencies also saw the problem, we believed it was the internal auditors who could describe it most clearly, and could mobilize a response.
We then gathered the heads of audit (and sometimes IT audit) from some of the largest publicly traded companies. Our goal was to assemble the auditors from top Fortune 50 companies, and have them uniformly say, "we all see a common problem, and it is causing significant economic harm. And we have a joint proposal for what we should do about it."
As mentioned in a previous blog post, the initial companies involved included General Motors, Wal-Mart, Hewlett Packard, Intel, Microsoft, Marathon Oil, Chevron Phillips Chemical, Business Objects, etc.
When those companies start screaming, people listen.
Next, Rope In Their External Auditors
Now that we had an impressive list of publicly traded companies all saying we had a problem, the next step was to engage their audit firms.
We had each one of the audit executives reach out to their IT audit engagement partners, and invite them to the GAIT summit. We selected and organized the companies to ensure that we had coverage of each of the Big Four firms (i.e., PwC, KPMG, E&Y and D&T). This was framed as a strong request to the Big Four firm, along the lines of, "I believe that it is very important for the relationship between our two companies that you personally attend this summit. And I'd like you to bring someone from your national practice, as well."
That last request was important, because the goal was not to change the IT scoping practices of, say, E&Y and Microsoft. Instead, the goal was to affect all of the engagements that E&Y was involved in. The national practices at the Big Four firms are usually responsible for establishing the standards, practices and procedures for the entire organization. They're typically some of the most senior and experienced partners, as well as promising staff members likely to become partners. Why would they want to attend?
This was probably one of the biggest obstacles to the GAIT initiative. How could encourage or compel the Big Four firms to participate? A cynical person would say that there was no real reason for them to get involved, as GAIT would do the following:
- Decrease billable hours in support of SOX-404 projects (i.e., "stop the SOX-404 gravy train")
- Increase the standards that they"™d have to adhere to (i.e., "create rope that they could get hung on")
Our solution was to make sure that Bill Powers from the PCAOB attended each of the GAIT Summits. The goal of GAIT transformed then to ensure that IT work performed in support of SOX-404 represented a continuation of the top-down, risk-based approach described in Auditing Standard 2, a publication published by the PCAOB. The implication is that the PCAOB would be very interested in any Big Four firms who did not want to participate in the GAIT process.
Voila: The GAIT Summits Began
Now we had assembled each of the constituencies required, each that could achieve a desired outcome out of a successful GAIT project.
- Internal auditors: accurately scope and substantiate IT controls in support of SOX-404
- Company management: ensure accurate financial statements and contain costs
- External auditors: stay out of trouble with the PCAOB
- Regulators: ensure that IT audit activities matched the spirit and intent of AS-2
Next up, I'll pose some thought-experiments on PCI scoping, and walk through the GAIT Principles.
 Thursday, January 26, 2012 at 1:54PM
Thursday, January 26, 2012 at 1:54PM 






